Image Description for DLSCCI-ECT-Downloader
Download Supply Chain Component Inventory is a lightweight inventory process to illuminate invisible risks in a download supply chain.
The following image appears on page 28 of the paper, under the heading "Human Factors" after the text "The following model considers the potential experience of a responsible end user through the event of downloading the product:":
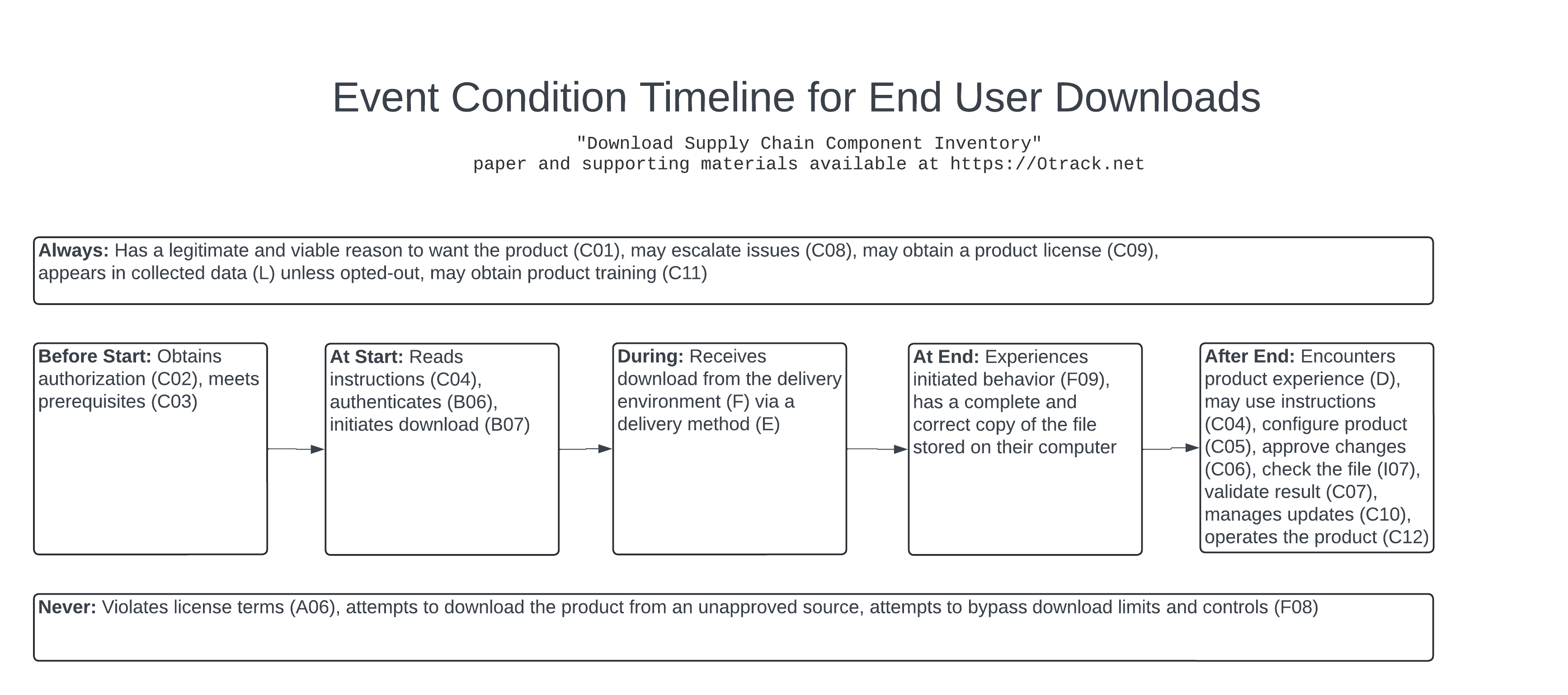
The following is a written description of all elements present in the image:
- This is a black and white image.
- The heading of the image reads "Event Condition Timeline for End User Downloads".
- A subheading of the image reads "Double-quoted Download Supply Chain Component Inventory Double-quoted paper and supporting materials available at https://0track.net".
- A graphic below the headings consists of a sandwich of boxes. There is one wide box across the top and one wide box across the bottom. Between the top and bottom boxes are five smaller boxes, side by side, and linked together with arrows from left to right.
- The top box is labeled "Always:" followed by "Has a legitimate and viable reason to want the product (C01), may escalate issues (C08), may obtain a product license (C09),
appears in collected data (L) unless opted-out, may obtain product training (C11)"
- Below the top is a middle row of five boxes.
- In the middle row of boxes, the leftmost box is labeled "Before Start:" followed by "Obtains authorization (C02), meets prerequisites (C03)". This is the first box in the row.
- An arrow leads from the Before Start box to the next box.
- In the middle row of boxes, the second box is labeled "At Start:" followed by "Reads instructions (C04), authenticates (B06), initiates download (B07)"
- An arrow leads from the At Start box to the next box.
- In the middle row of boxes, the third box is labeled "During:" followed by "Receives download from the delivery environment (F) via a delivery method (E)"
- An arrow leads from the During box to the next box.
- In the middle row of boxes, the fourth box is labeled "At End:" followed by "Experiences initiated behavior (F09), has a complete and correct copy of the file stored on their computer"
- An arrow leads from the At End box to the last box in the row.
- In the middle row of boxes, the fifth box is labeled "After End" followed by "Encounters product experience (D), may use instructions (C04), configure product (C05), approve changes (C06), check the file (I07), validate result (C07), manages updates (C10), operates the product (C12)". This is the last box in the row.
- Below the middle row of boxes is a bottom box.
- The bottom box is labeled "Never:" followed by "Violates license terms (A06), attempts to download the product from an unapproved source, attempts to bypass download limits and controls (F08)"
- This concludes the list of elements present in the image.
Additional content available at: 0track.net
